As organizations mature, identity governance administration (IGA) becomes equally important. You need to tracking, reviewing, and justify every user's permissions to pass compliance requirements.
Okta launched their Okta Identity Governance (OIG) product in 2022 to tackle this problem.
In this article, we'll cover what it does well, where it struggles, and whether it's worth it - particularly if you're already using Jira Service Management for access requests.
What is Okta Identity Governance?
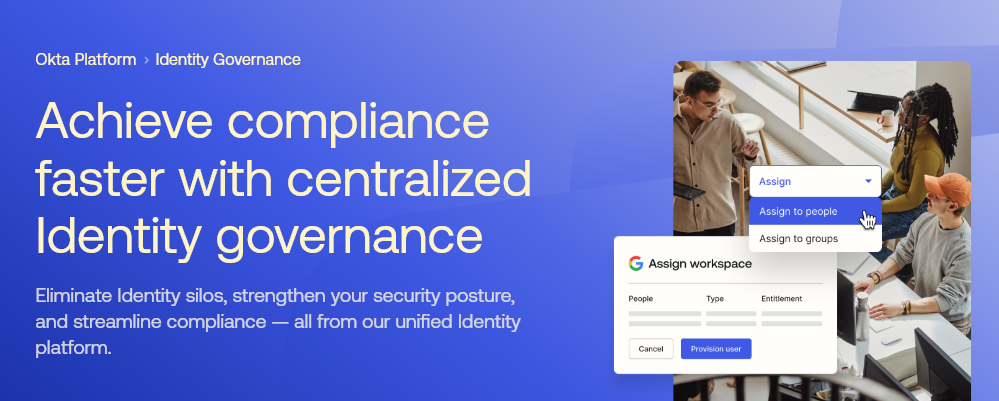
Okta Identity Governance adds IGA capabilities to regular Okta. It bundles three Okta offerings: Okta Workflows, Lifecycle Management (LCM), and Access Governance.
You purchase Okta identity governance as a subscription add-on to your existing Okta tenant. Once activated, new governance features appear in your Okta admin console without disrupting your existing SSO, MFA, or user provisioning.
Core Features of Okta Identity Governance
Okta Workflows
The automation engine of Okta identity governance. You can build low-code or no-code flows for custom actions like provisioning/deprovisioning users, triggering access reviews, or kicking off approval workflows when someone requests privileged access.
Lifecycle Management
This handles the "joiner-mover-leaver" process that's central to identity governance for access management. Okta identity governance can automatically provision access to birthright apps upon onboarding. It can then adjust that access when they change roles or tasks, and deprovision their accounts and permissions when they leave.
It can also take care of other ILM processes like profile mapping, directory integration, and SCIM (System for Cross-domain Identity Management).
Access Governance
LCM and Okta Workflows work in sync with OIG's Access Governance for requesting, approving, and reviewing access requests to your organizations applications. It covers the following:
Access Requests
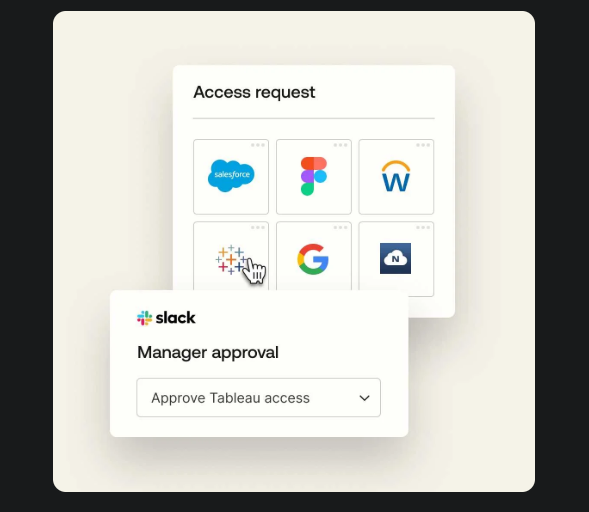
Instead of emailing IT, users can browse available apps and roles, click to request access, and check the approval status via the End-User dashboard.
The requests are automatically routed to the right approvers based on what's being requested, like requiring just manager approval for basic apps but adding security team approval for admin roles. This self-service access request portal is embedded in the normal Okta interface.
Separation of Duties
Okta identity governance also enforces Separation of Duties (SOD). This stops people from having permissions that can be risky together, like preventing the same person from being able to create invoices and approve payments.
You set up rules for risky permission combinations, and OIG automatically blocks any request access that would break these rules or flags them for special approval. It also alerts managers during access reviews when someone has built up conflicting permissions over time.
Entitlement Management
Entitlement Management lets you manage app-specific roles and permissions from the Okta admin console.
You can set up policies that automatically give people certain roles based on their job title or department, or manually assign specific permissions to individual users to make sure everyone has exactly the right level of access they need.
SCIM with entitlement
For apps with SCIM support, Okta Identity Governance can automatically sync these entitlements back and forth with the actual application. For example, assigning "Salesforce Marketing User" role in Okta actually creates the role assignment in Salesforce itself.
Access Certifications
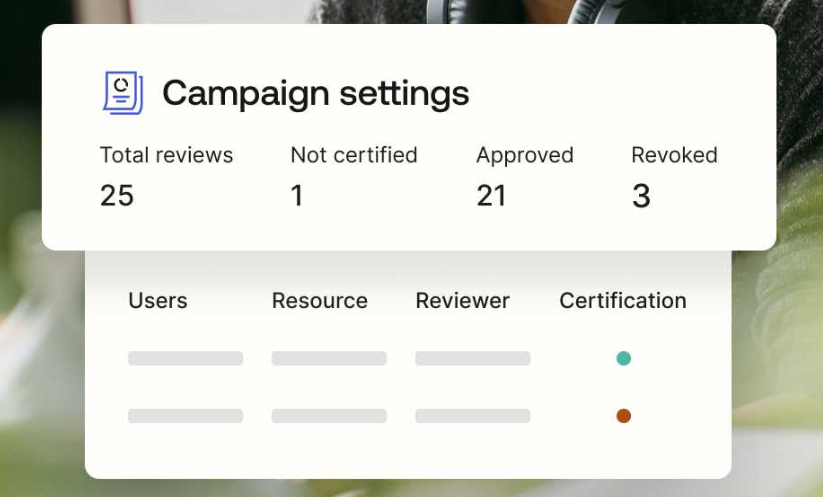
You can set up access certification campaigns by choosing which apps and users to review, who should do the reviewing, and how long the access certification campaign will run. Then OIG sends out the review tasks to managers and tracks their progress until completion.
Reports, APIs, and System Log Events
Finally, Access Governance rounds out with:
Auto-generated audit reports
Okta identity governance provides four specific report types: Past Campaign Details, Past Campaign Summary, Past Access Requests, and User Entitlements reports for auditors. Great if you frequently use the same types of reports for access certification.
okta Identity Governance APIs
The let you programmatically create access certification campaigns, assign entitlements, and pull compliance data from connected apps.
System-triggered workflows
System event logs can be configured to trigger events using Okta Workflows. For instance, events like "access request approved," "access certification campaign completed," or "entitlement revoked" can automatically send Slack alerts or execute the next step of your access certification campaigns.
Pros and Cons of Okta Identity Governance
As of 2025, reviews for Okta Identity Governance are mixed. Users generally like how it streamlines basic IGA tasks like automating access requests, running access certification campaigns, and syncing with Okta's existing user management.
Pros
- Seamlessly adds identity governance to Okta's IAM platform
- Familiar Okta interface reduces training time
- Ability to request access via tools like Slack is convenient for users
- Automation makes access certification campaigns more efficient
- Pre-built reporting templates simplify audits
- Has connectors for hundreds of business apps
Cons
- "No-code/low-code" workflows still need custom coding for anything complex
- System often crashes when trying to add multiple users to roles at once
- Limited functionality with non-Okta systems
- Can't properly track access request history internally - you'll need external reporting
- Doesn't integrate natively with common ITSM platforms like Jira Service Management
- No access request support for non SAML SSO apps
Okta identity governance works best for existing Okta customers who want basic governance without vendor sprawl.
If you need advanced IGA features like custom access expiration or proxy access requests, you'll probably outgrow it fast.
Is Okta Identity Governance Good for ITSM Teams?
It can be a poor fit for organizations on Jira Service Management and other major ITSM platforms.
For instance, OIG's Jira integration can only process formal request types. There's no native support for Jira's access request conditions, which lets you restrict access to certain Jira projects and set rules for granting/revoking permission (fundamental to identity governance and access certification campaigns).

This means you can't handle all your access requests on JSM - only the ones that use the more complex request type setup.
And sure, you can run access certification campaigns with OIG and view the report on their web interface. Unfortunately, exporting that data to CSV, Excel, or other formats is not available
This creates huge security gaps for ITSM teams who can't:
- Import access certification campaign results into JSM for tracking
- Create JSM tickets for failed reviews that need follow-up
- Generate combined reports showing both access reviews and related IT service requests
- Maintain a single source of truth for all IT operations including governance
So JSM teams end up with governance data stuck in Okta and operational data in JSM, making it hard to get a complete picture of IT activities.
Other issues like not letting users to request specific app roles without exposing Okta group names be frustrating, too.
A Better Alternative to Okta Identity Governance
Multiplier's native Jira integration makes it more practical for for organizations that use Jira Service Management.
Unlike OIG, it weaves access request workflows inside JSM. Your existing workflows can now trigger access certification campaigns, enforce least privilege, generate audit reports, and other identity governance work.
If you want to implement IGA but not sure where to start, book a demo and let's hop on a call. We'll give you a quick audit to see how Multiplier can help your team. No hard sell.
You can also install Multiplier from Atlassian Marketplace for a free 14-day trial.
Lastly, here's a more detailed breakdown of Multiplier as a complete alternative to Okta Identity Governance.









